Microsoft Details Mac OS X Malware That Exploits Office Vulnerability
Malware that targets Mac OS X machines is becoming widespread and most major companies have come to realize that Apple products are not as safe from malicious viruses as they were once. As expected, Microsoft also came forward to provide an example of a Mac OS X threat.
Image Credits: Microsoft
This particular malware, identified as Exploit:MacOS_X/MS09-027.A, leverages a remote code execution vulnerability in Microsoft Office, which was addressed by the company back in 2009.
Although the infection rates are not as widespread as in the case of the now-infamous Flashback Trojan, the company’s security experts reveal that there are still a number of computer owners who have failed to apply the security update, thus putting their assets at risk.
So how does the infection work?
First of all, it has been determined that the exploit works only on Snow Leopard or earlier versions of the operating system because starting with Lion, the memory address targeted by the malware is read–only.
As the diagram shows, the stack-based buffer overflow vulnerability is used to corrupt a local variable, which is later utilized to deploy the “stage 1” shellcode to a specific area.
This “stage 1” shellcode then leads to the “stage 2” shellcode, which is the location in the memory where the actual infection occurs.
“Stage 2” creates a number of three files: tmp/launch-hs, /tmp/launch-hse, and /tmp/file.doc. The first file actually contains a shell script or an executable which launches /tmp/launch-hs and and opens /tmp/file.doc.
The latter is actually a decoy document that’s designed to trick users into believing that there’s nothing malicious involved.
/tmp/launch-hse is the main payload file that, once it’s executed, starts communicating with the malware’s command and control server.
“Statistically speaking, as this operating system gains in consumer usage, attacks on the platform will increase. Exploiting Mac OSX is not much different from other operating systems. Even though Mac OSX has introduced many mitigation technologies to reduce risk, your protection against security vulnerabilities has a direct correllation with updating installed applications,” Jeong Wook Oh of the MMPC concluded.
Microsoft Details Mac OS X Malware That Exploits Office Vulnerability
Microsoft Details Mac OS X Malware That Exploits Office Vulnerability was published by . We hope that information about Microsoft Details Mac OS X Malware That Exploits Office Vulnerability very usefull for you. You can get another usefull information related with Microsoft Details Mac OS X Malware That Exploits Office Vulnerability at our sharing post in facebook, twitter and etc.. Warm regard from us.
 Tweet
Tweet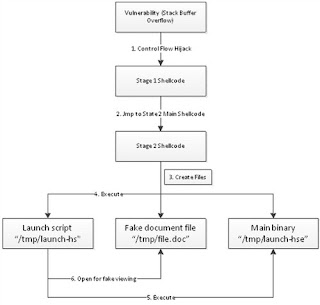



0 comments:
Post a Comment